[ad_1]
Disclosure: The views and opinions expressed here belong solely to the author and do not represent the views and opinions of crypto.news’ editorial.
2023 has been characterized by bearish conditions flattening markets and a heavy focus on regulation and compliance through the lens of the large-scale collapses and fraud incidents in 2022.
However, things are rarely quiet for long in this industry, and change is already in the air. While the question of jail time for Sam Bankman-Fried and Changpeng Zhao may still be outstanding, the drama of the legal battles appears to be largely settled, and the sector is buzzing with anticipation of a new bull market as it looks ahead to the year ahead. An expected spot ETF approval and the upcoming Bitcoin halving are both adding to rising speculation.
While a change in market conditions is good news, it inevitably brings fresh challenges for web3 security professionals. Here are three macro trends that will shape the web3 security landscape in the upcoming year.
Hacks and scams on the rise
Cybercrime activity in web3 has an unfortunate tendency to follow the ebb and flow of the markets. According to the US Federal Trade Commission, losses to crypto scams in 2021, when Bitcoin (BTC) reached its all-time high, were sixty times the levels seen in 2018. However, the most recent data from Chainalysis suggests that scam activity dropped by as much as 77% in 2023 compared to the previous year.
However, Chainalysis notes that certain types of scam activity, notably impersonation scams, are actually showing an increase. Furthermore, if the market does pick up in 2024—as many analysts believe it will—scammers will once again be drawn to the financial opportunities in crypto.
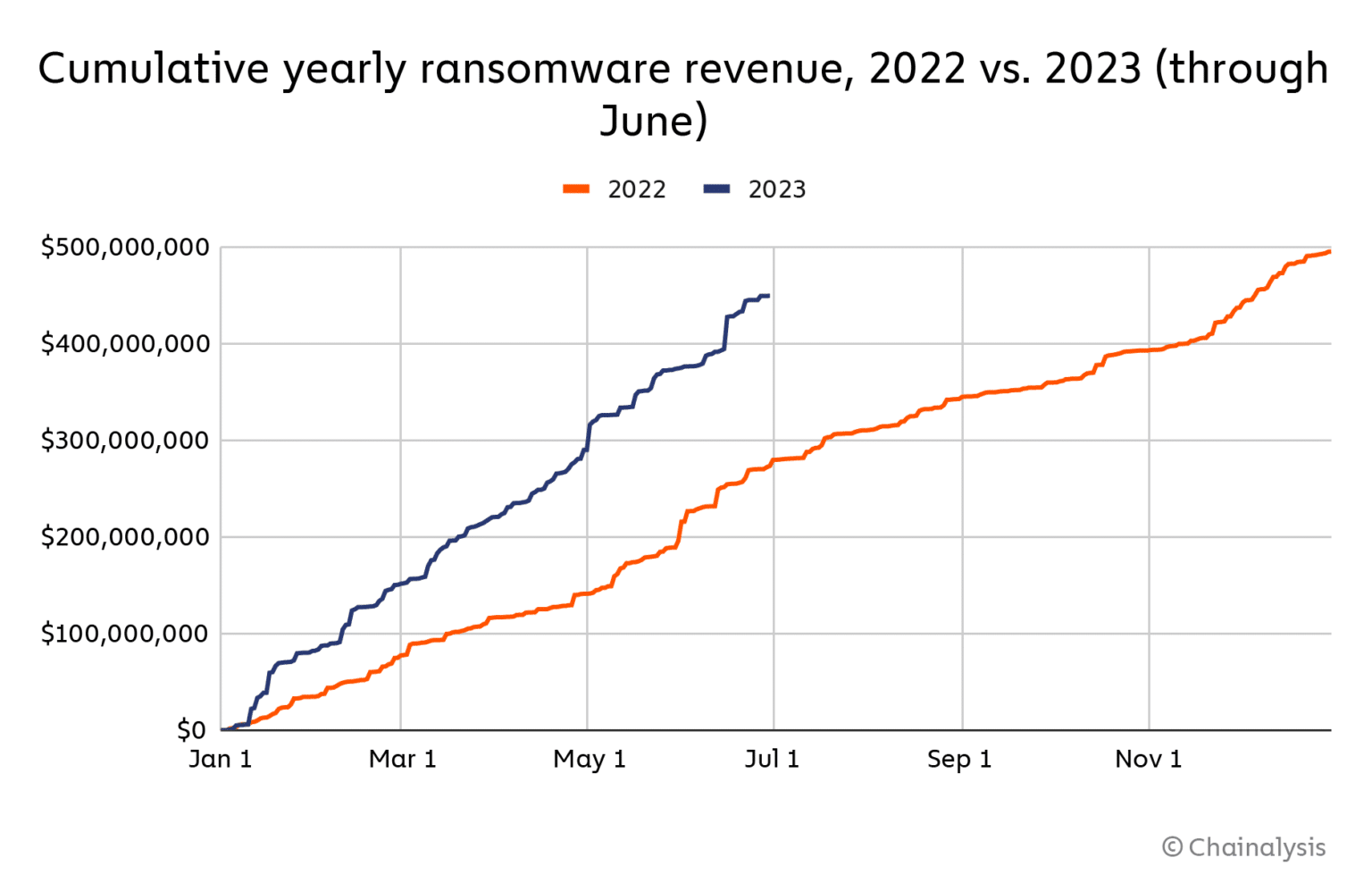
Ransomware is rising in 2023 | Source: Chainalysis
Therefore, we’re likely to see not just an increase in the number of scams but also increasing levels of sophistication and consolidation in scammer activity. One example is advanced evasion techniques designed to cloak fraudulent actions. These include spoofing, which involves masquerading malicious entities as benign by mimicking legitimate features; morphing, where scammers change a smart contract’s behavior based on context; and obfuscation, which makes harmful code difficult to detect and understand.
Off-chain signatures, which allow transaction signing without broadcast to the blockchain network, are another area of vulnerability to be preyed on by scammers. In signature phishing scams, the attacker will set up a scenario such as a fake dapp requiring the user to generate an off-chain signature for a transaction that looks legitimate. One example could be providing a signature to list an NFT, where the user is inadvertently signing a transaction that will allow the scammer to drain all NFTs from their wallet.
The recent shutdown of ‘draining as a service’ Inferno Drainer, a toolkit that equips fraudsters with the technical means of stealing from wallets, is undoubtedly good news for the industry. However, it’s unlikely to be the last of its kind, given it’s reportedly responsible for stealing $80 million worth of crypto this year alone. We can expect to see more of this kind of consolidation activity among scammers in 2024.
Expansion of web3 cybersecurity capabilities
Just as fraud activity is set to become more sophisticated, the web3 cybersecurity ecosystem is also gaining new features and tools to help fight back against scams and illicit activity. Attack detection protocols have already identified hacks that had taken place, including the $33 million theft from SushiSwap in April 2023, before the funds were withdrawn.
On-chain extensions, similar to wallet extensions, can further support threat prevention by carrying out risk monitoring using on-chain data in real time, providing an additional layer of protection for users and protocols.
Furthermore, on-chain data and analytics will take on new dimensions thanks to the increasing involvement of TradFi and institutional liquidity, which will bifurcate the sector. The open, pseudonymous, and permissionless protocols that dominate the industry today will increasingly operate alongside permissioned, compliant, and secure counterparts. The additional layers of data and information will enhance the ability and accuracy of risk profiling—benefits that can be further compounded by further advances in AI and machine learning.
A more strategic web3 cybersecurity approach
With each market cycle, the maturity of the crypto and web3 space grows. Projects and companies are increasingly aware that they must go above and beyond a code audit to demonstrate a commitment to cybersecurity and stay one step ahead of fraudsters. A comprehensive strategy that starts with secure design and moves all the way to monitoring and threat prevention solutions is required.
Threat handling should take a holistic approach to risk, using preventive measures such as asset segregation and transaction screening, combined with mitigation measures like automated circuit breakers, along with reactive relief such as insurance.
To meet this demand, providers such as Forta have developed cybersecurity tools such as blockchain scam detectors and attack detectors that are designed specifically for the needs and threats facing Web3 operators.
Moving forward into 2024, the palpable sense of optimism is long-awaited and much deserved. However, mindful of the risks that increasing wealth and liquidity will bring, Web3 firms must be ready for a new wave of threats facing the industry and have all their cybersecurity guardrails in place to keep assets and users safe.
[ad_2]
Source link

